Access Tokens
Access Tokens in GraphQL Hive are secure credentials used to authenticate API requests and automate actions without using personal login details.
With Access Tokens, you can perform tasks such as:
- Publish schemas etc. with the Hive CLI
- Report usage data (SDK or HTTP)
- Access the public Hive Console GraphQL API for managing resources and exporting data
Access Tokens in GraphQL Hive support granular permission scopes, allowing you to define exactly what actions a token is allowed to perform and on which resources (project, target, service or app deployment). This helps enforce the principle of least privilege, ensuring tokens only have the access they need - and nothing more.
For example, a CI pipeline that publishes schemas only needs the “Publish Service” scope. There’s no need to grant more permissions.
Three types of access token exist.
Organization Access Tokens. These are scoped at the organization level and managed by organization administrators. They are typically used to integrate with external tooling for provisioning resources such as projects and users.
Project Access Tokens: These are scoped at the project level and can be managed by any project member with sufficient permissions. They are commonly used for self-service operations such as CI/CD or CLI workflows.
Personal Access Tokens (PATs). These are scoped to individual organization members and can be
enabled or disabled on a per-user basis. They are primarily used for personal or local development
tasks, such as running hive dev.
Important: Treat access tokens like passwords. Keep them secret and revoke them immediately if compromised. Monitor token usage regularly and revoke unused tokens to maintain security.
Access Token Type Overview
Depending on the use-case you want to use different access tokens. All the access tokens share the following properties:
- Assigning granular permissions.
- Assigning granular resources in a hierarchical structure.
Organization Access Tokens
- Require the
Manage organization access tokens(accessToken:modify) permission (assignable to users roles). - Can technically be used to elevate permissions, so usage should be restricted.
- Recommended only for organization administrators, typically for third-party integrations that provision or manage resources at the organization level.
Project Access Tokens
- Require the
Manage project access tokens(projectAccessToken:modify) permission (assignable to user roles). - Manage access within a specific project.
- Most access tokens should fall under this category.
- Recommended for CI/CD pipelines performing actions such as schema publishing or schema checks.
- Organization administrators can view and revoke all project access tokens from the organization settings.
Personal Access Tokens (PATs)
- Require the
Manage personal access tokens(personalAccessToken:modify) permission (assignable to user roles). - Organization administrators can view and revoke all personal access tokens in the organization settings.
- The permissions and resources of a PAT are a subset of the member’s role permissions.
- If a member’s role permissions are downgraded, the PAT automatically reflects the change.
- Recommended for local CLI usage, such as running
hive devorhive check. - Not recommended for CI/CD - use Project Access Tokens instead.
- Removing a user from the organization automatically deletes their PATs.
- Removing the
Manage personal access tokens(personalAccessToken:modify) permission temporarily disables all tokens issued by that user until the permission is restored.
Create an Access Token
Depending on the type of access token you are creating, navigate either to the organization settings
Access Token subpage for creating Organization Access Tokens, the organization settings
Personal Access Tokens subpage for creating Personal Access Tokens or the project settings
Access Tokens subpage for creating Project Access Tokens
Ensure sufficient permissions
To create an Access Token in GraphQL Hive, you must have the Manage Access Token permission at the
organization level. Tokens are created at the organization level and can be managed (created or
deleted) by any user with sufficient permissions.
Navigate to Access Token Settings
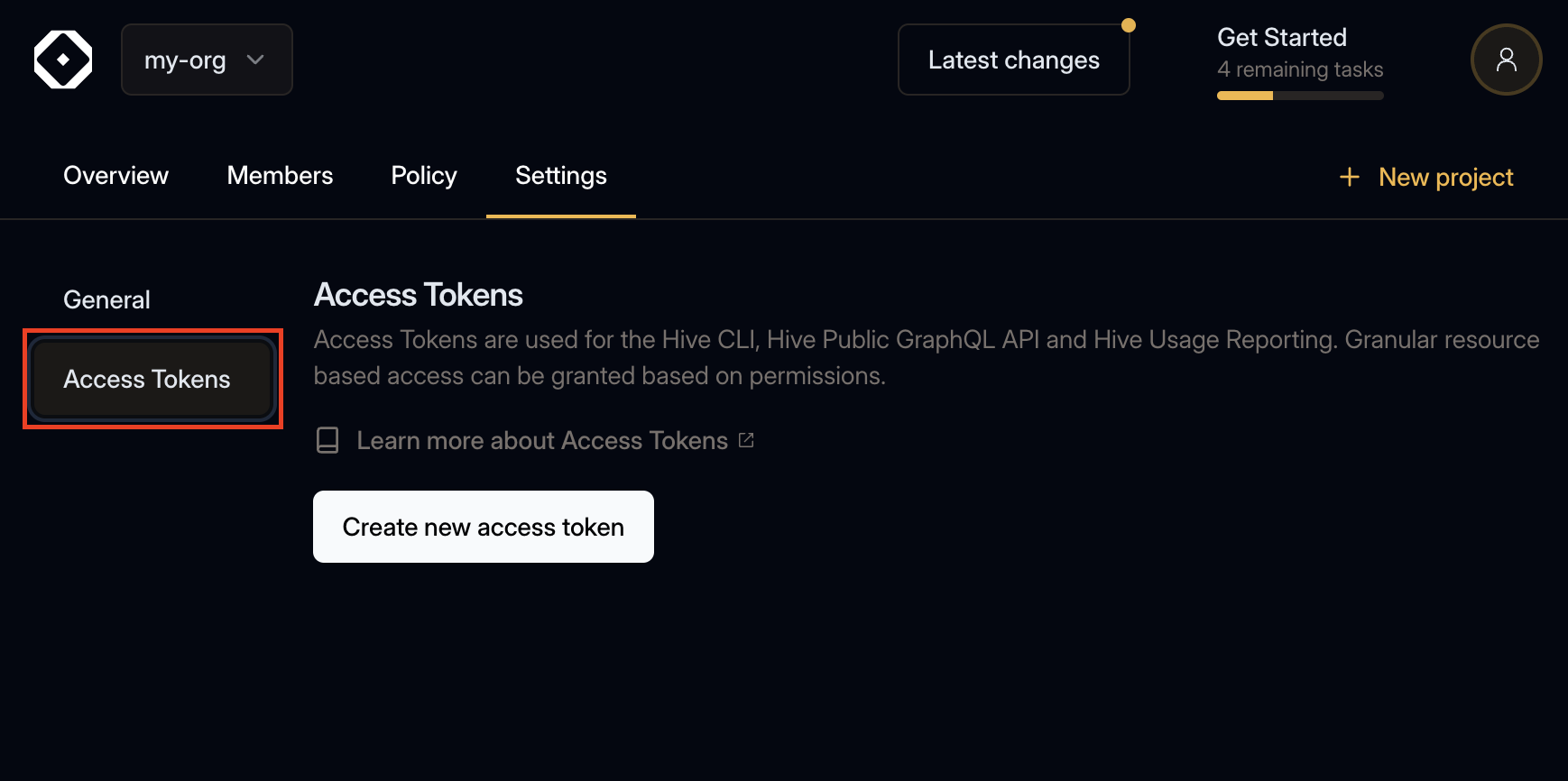
Go to the Settings tab of your organization and open the Access Tokens section.
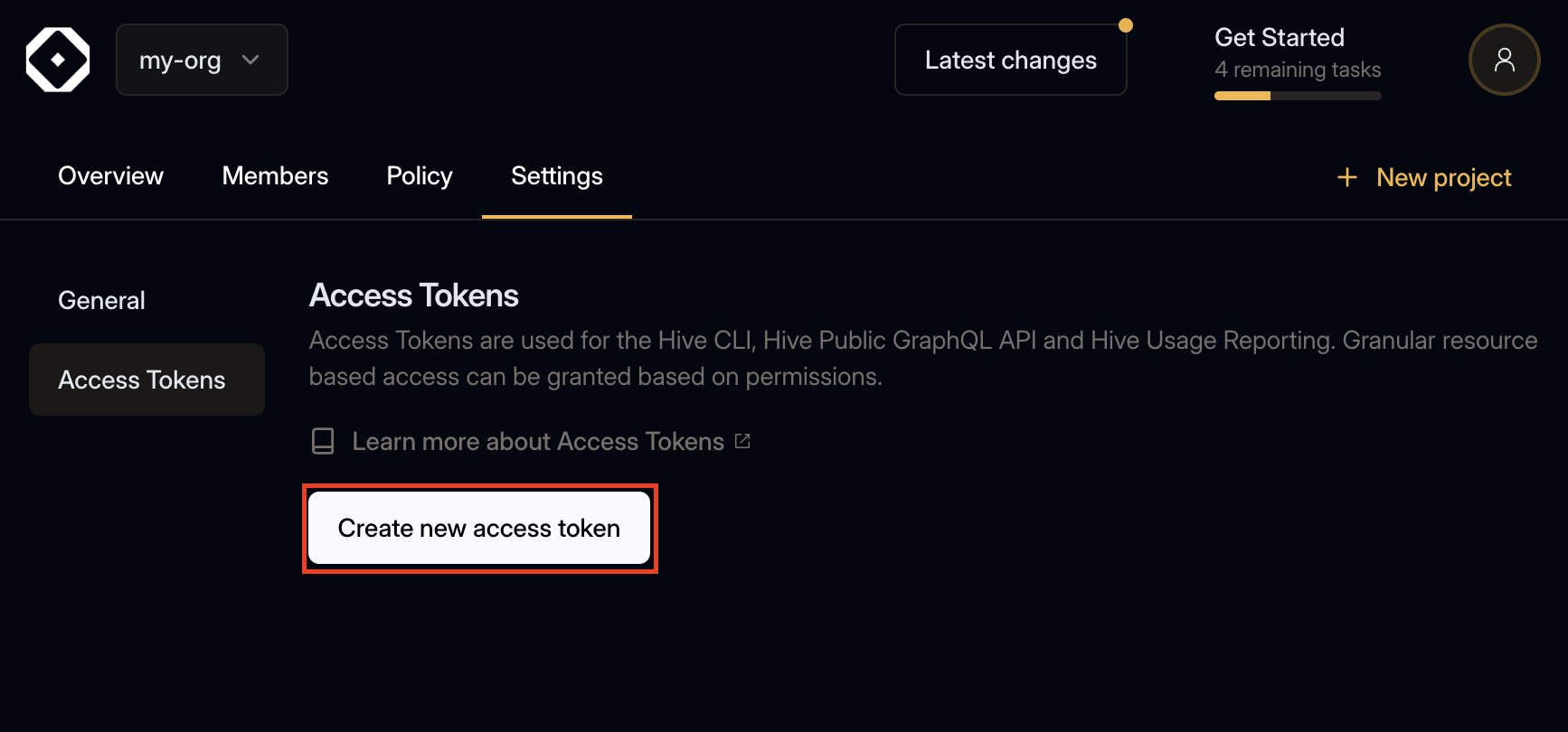
Click Create new access token.
Enter General Information
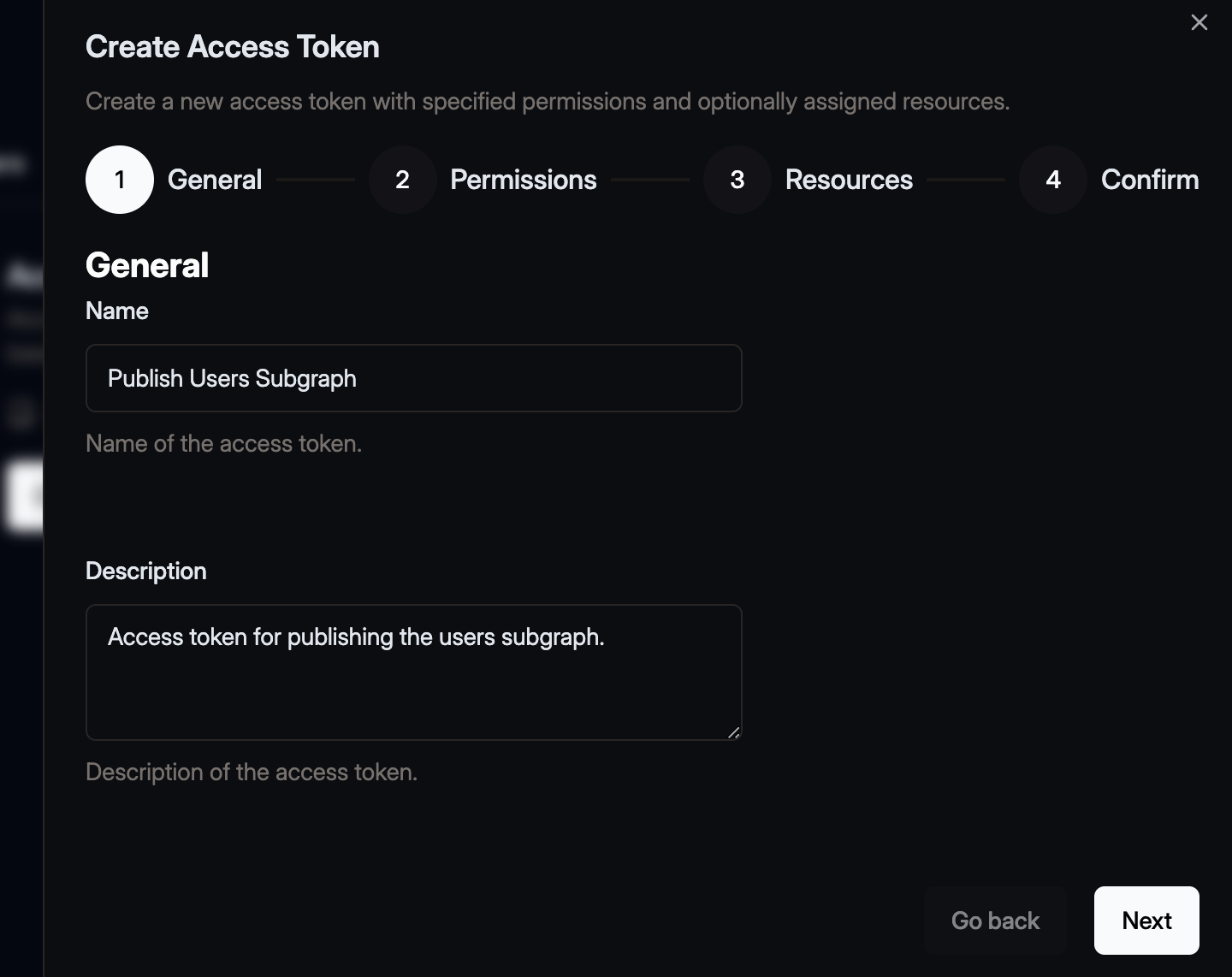
Provide a clear title and description to help your team understand the token’s purpose.
Confirm your selection by clicking Next.
Select Permission Scopes
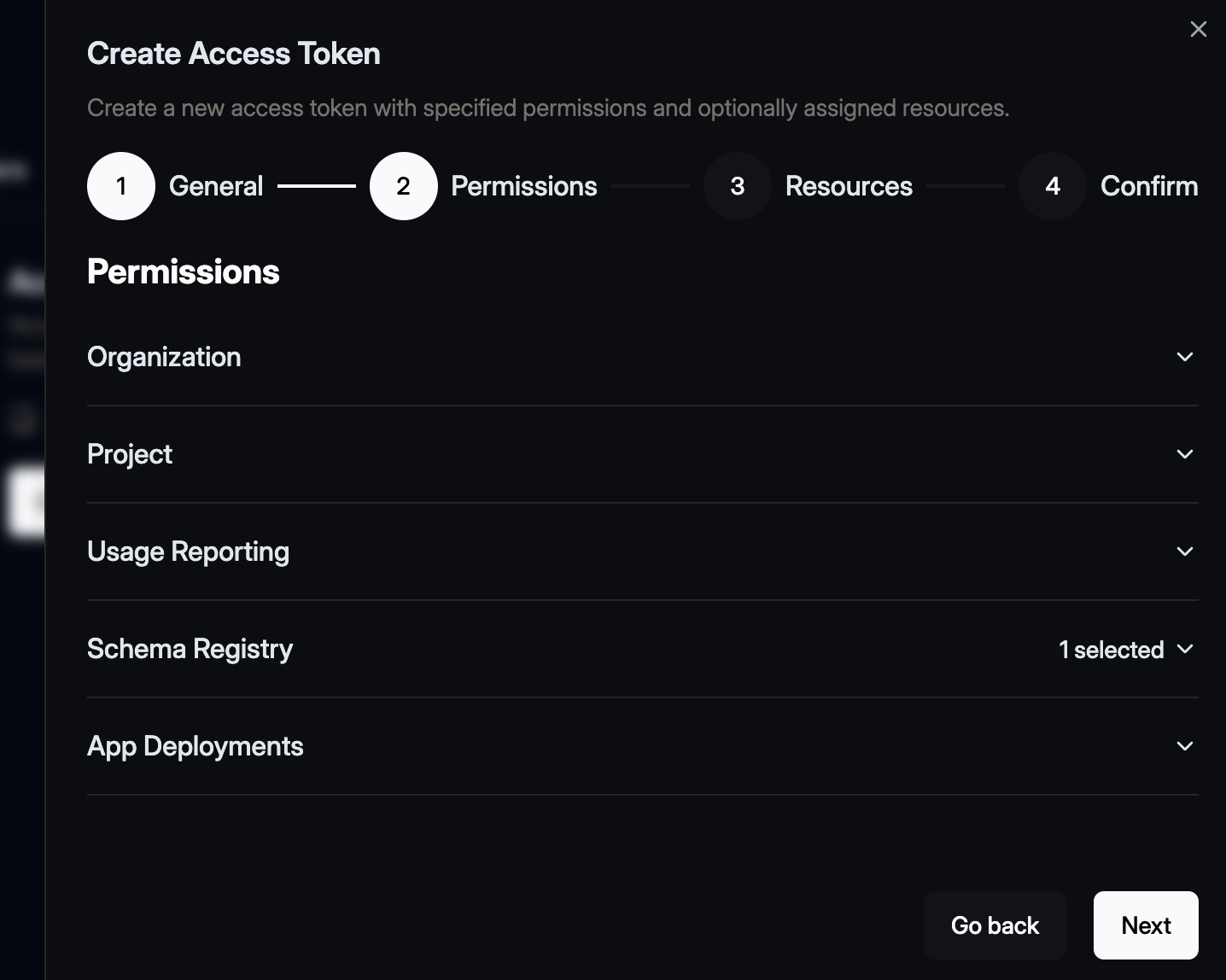
Choose the permissions the token should have.
Tip: Follow the principle of least privilege by only selecting the scopes necessary for the token’s purpose.
Confirm your selection by clicking Next.
Select Resources
Decide if the token should have access to:
- All resources in the organization, or
- Only specific projects/targets/services/apps.
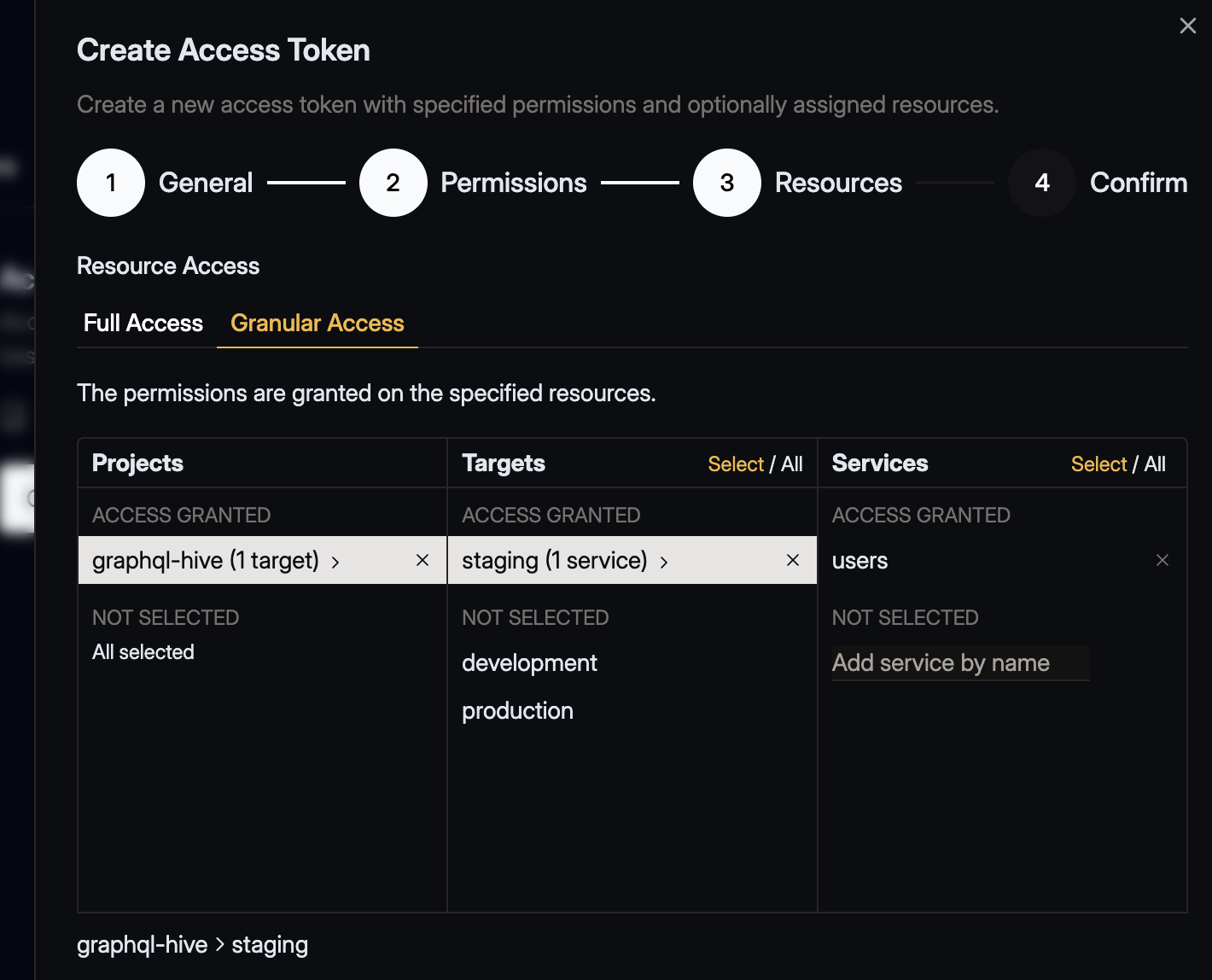
Confirm your selection by clicking Next.
Review and Create
Carefully review all the details—title, description, scopes, and resource assignments.
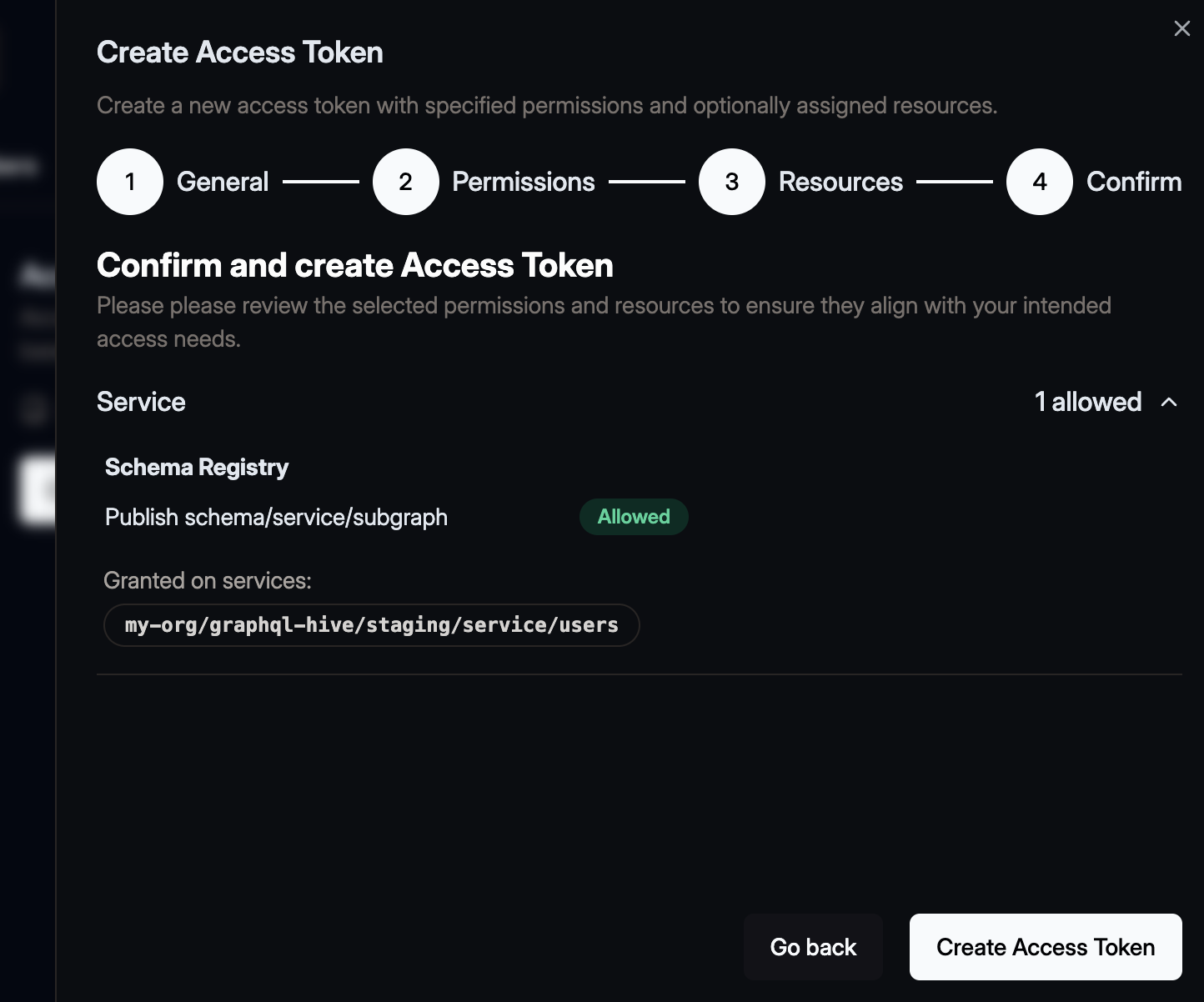
When you’re ready, click Create Access Token.
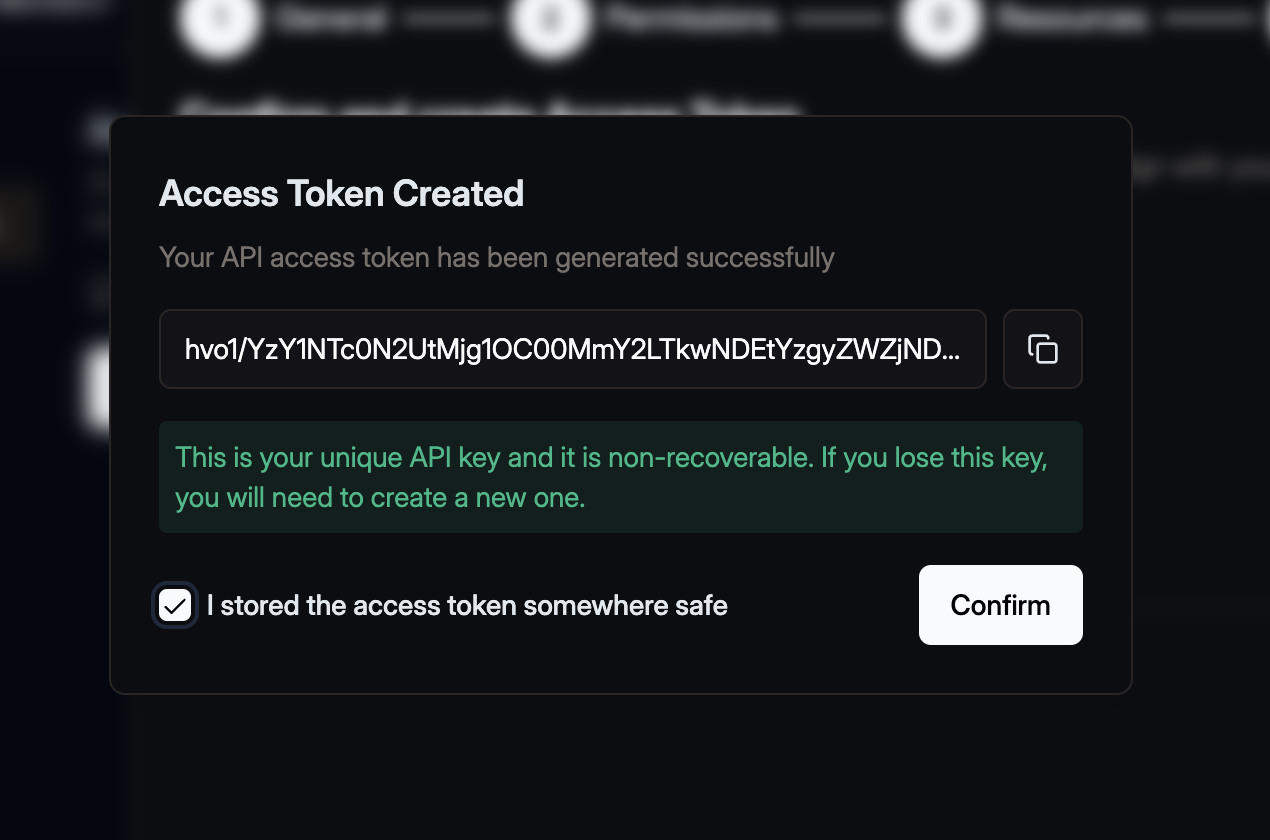
Save your Token
After creation, your access token key will be displayed once.
- Copy the token and store it securely (for example, in a secrets manager).
- You won’t be able to view it again.
- Use this token to authenticate with Hive’s CLI or API.
- Never share your token and immediately revoke it if it becomes compromised.
Deleting Access Tokens
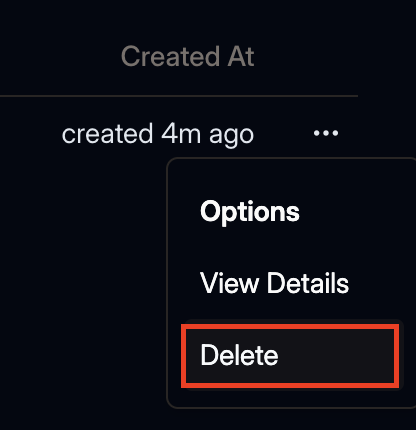
Within the Access Token overview, click the three dots icon for opening the context menu.
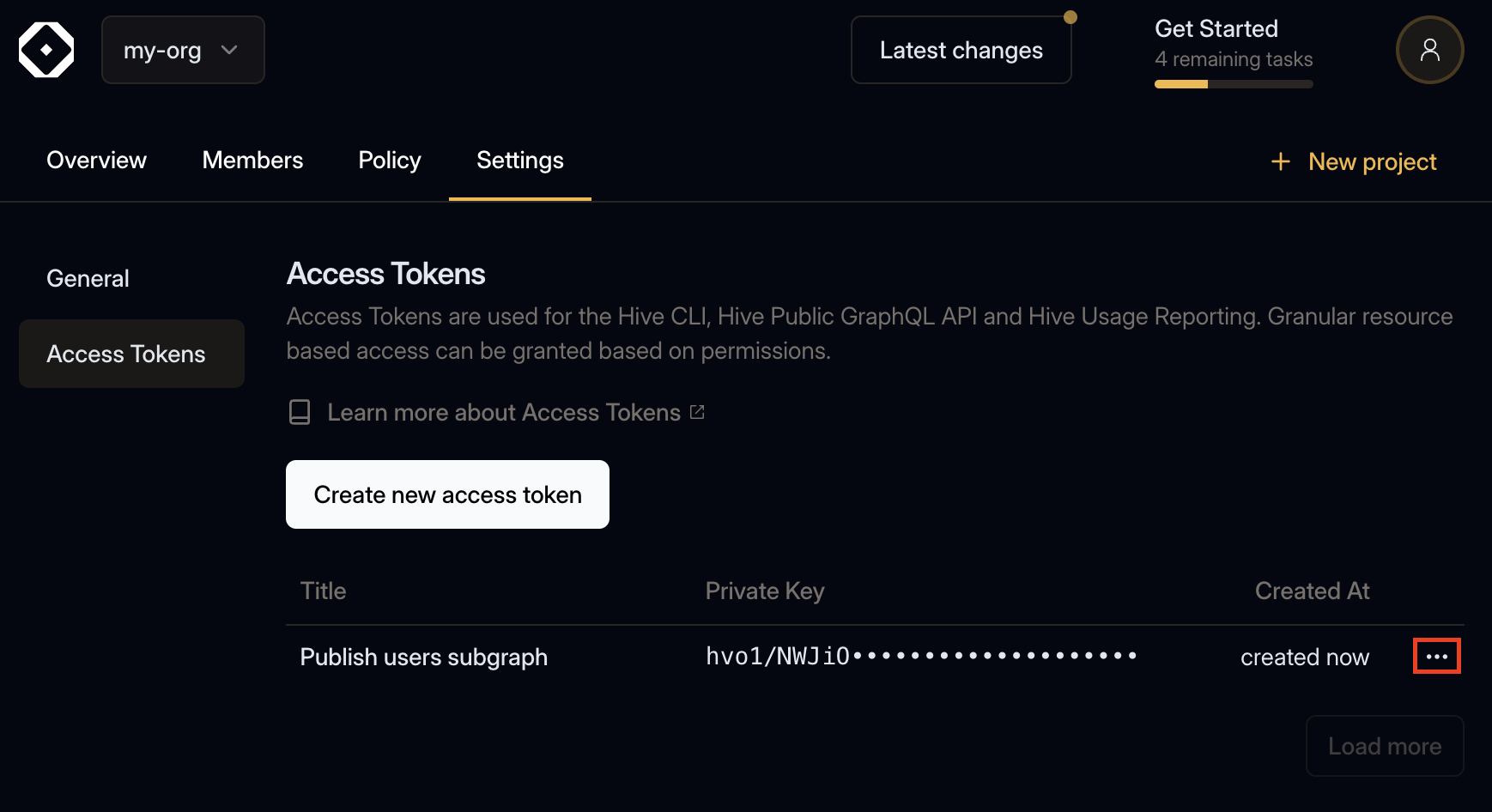
Within that menu, click the Delete menu item.
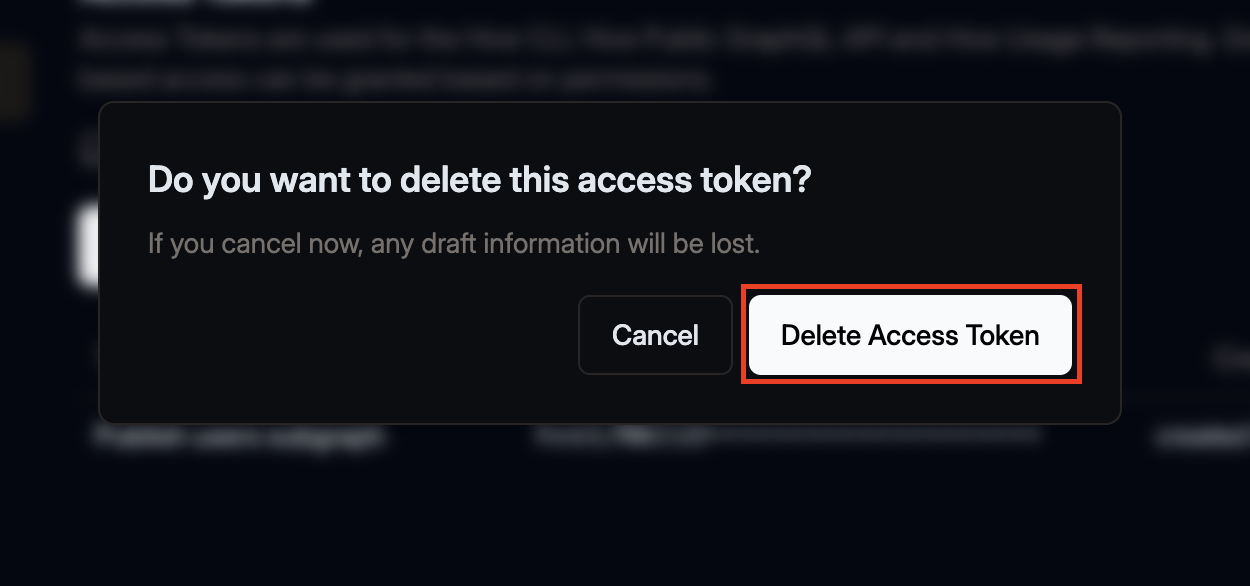
Confirm the deletion within the dialog.
Updating Access Tokens
Updating access tokens is currently not possible. Please instead create a new access token with updated permissions, replace the usages of the old access token and then delete the old access token.